Malware can cause websites to fail to load, redirect users or can be used to send spam emails. Whilst there are paid services, let me show you how you can resolve this issue in 3 simple steps for free:
If you would rather not worry about tinkering with files and code, I provide a Malware Removal Service. Please contact me for more information.
Frequently Asked Questions
What is malware?
Malware (malicious software) is any software intentionally designed to cause damage to a computer, server, or website.
How did the site get infected?
A critical vulnerability in File Manager plugin affected 700,000 websites in September 2020. It allowed hackers to gain complete access to the websites and infect them.
Other reasons for sites to get infected include
How to remove malware?
Pay for Malware removal services available from Sucuri, contact me, or follow these 3 steps illustrated below.
How can we avoid malware?
Use few plugins as possible – choose the plugins wisely.
Keep WordPress and plugins up to date.
Backup constantly (in addition to daily backups by hosting provider). I use All-in-one WP Migration to take regular backups.
Choose good web host – I use and recommend SiteGround (affiliate link). It is worth investing $2 per month in SG Site Scanner to ensure that malware and spam is detected instantly before hackers have a chance to do any damage.
Limit the number of users with full admin access to 2 or 3.
To prevent brute force attacks… do not create usernames and passwords that can be easily guessed.
– For example, it is common practice to create an account with ‘Full access’ called ‘admin’. To mitigate this, create a user account with username ‘admin’ and give it ‘Subscriber’ access.
– Use strong passwords. Avoid using the same password on multiple sites.
Identify the malware
A good host like SiteGround constantly monitors your sites and backs them up daily. When malware is detected, it is contained by your web host by limiting access to the website.
A critical vulnerability in File Manager plugin affected 700,000 websites in September 2020. It allowed hackers to gain complete access to the websites and infect them.
This was the first time any of my clients sites were hacked. The site https://iuuriskintelligence.com/ had this very popular plugin installed and hence got hacked. I received an email from SiteGround confirming the hack. This is the first step.
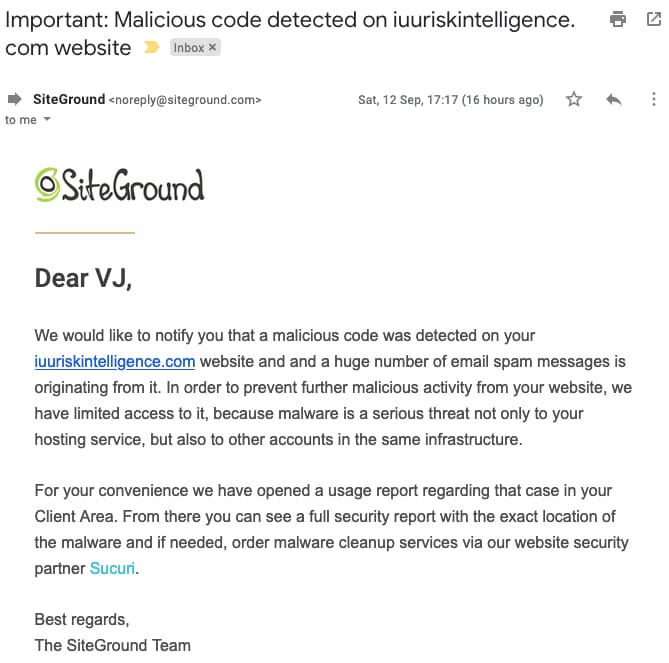
Confirm the severity of the hack.
Ask your hosting provider to provide you with severity of the infection. SiteGround staff are very helpful and they provided a list of infected URLs. Login to your hosting backend to see the Malware infected URLs for the domain.
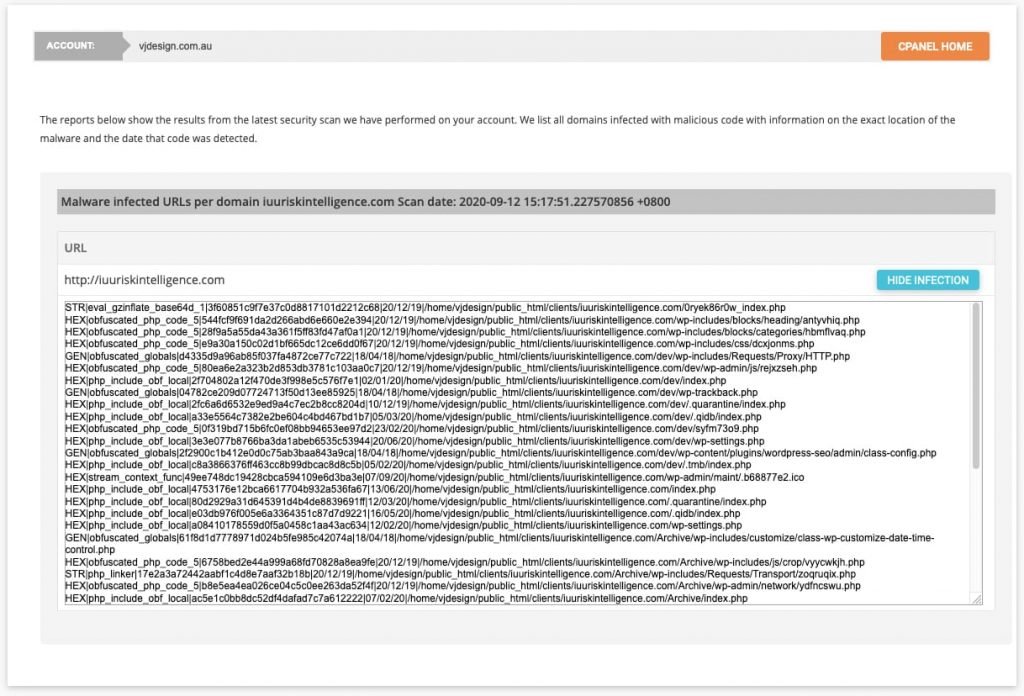
Clean the malware
The first step is to prevent access to hackers – your web host will do this automatically to prevent more damage to your site and to prevent other sites on their servers from getting hacked. If your web host has not done so, you would need to Block all access and allow only your IP address.
Remember to take a backup before you start removing malware.
Start the process by copying the infected URL list to a code editor or simple text editor (like Notepad or TextEdit). As you clean or delete the infected files, remove the same from your list.
Login to your hosting provider, either download your files using FTP or use the File Manager tool from cpanel.
I noticed that there were 3 types of infections and the treatment is dependent on the type of infection:
1. Infected file full of malicious code (not a regular WordPress file)
I noticed that there were several files that were full of malware code (no WordPress code or php at all). Such files had gibberish names that made no sense e.g. y553s0ry.php and gsdfrwf4.ico
Treatment: Having checked that the file is just I simply deleted such files via File Manager (or FTP). To delete the file, select the file and choose Delete.
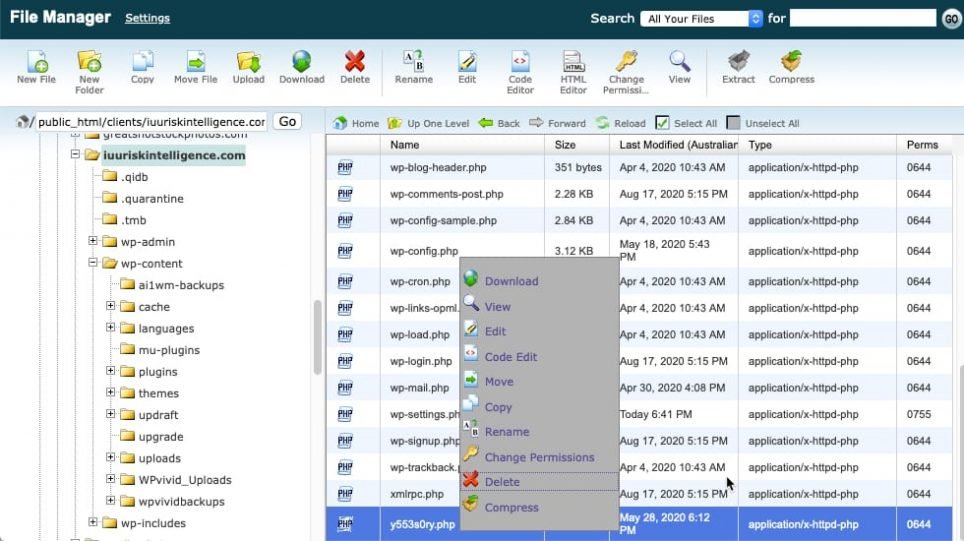
Pro Tip: Notice in the screenshot above that infected files have a more recent ‘Last Modified’ date.
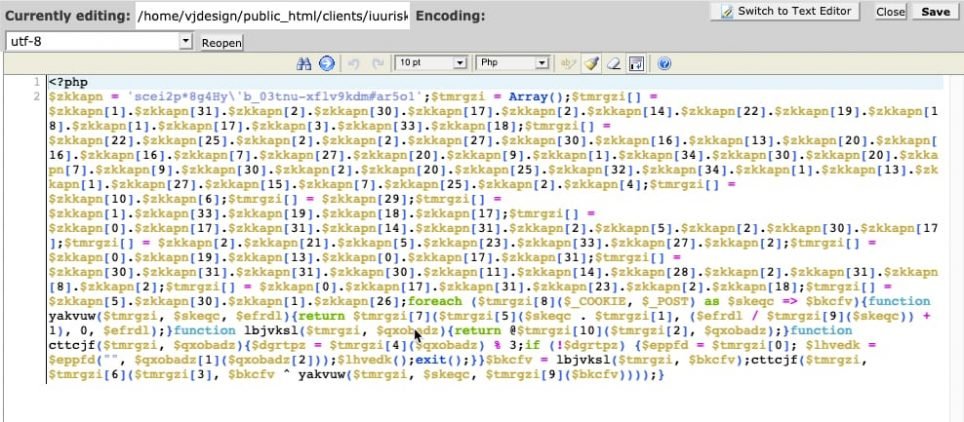
2. Infected file with minimal malicious code
I noticed that some php files were infected very minimally. I noticed that such malicious code started just after opening <?php tag on line 2 and before the opening comments. A good indication is that most WordPress (php) file start with detailed comments as indicated below.
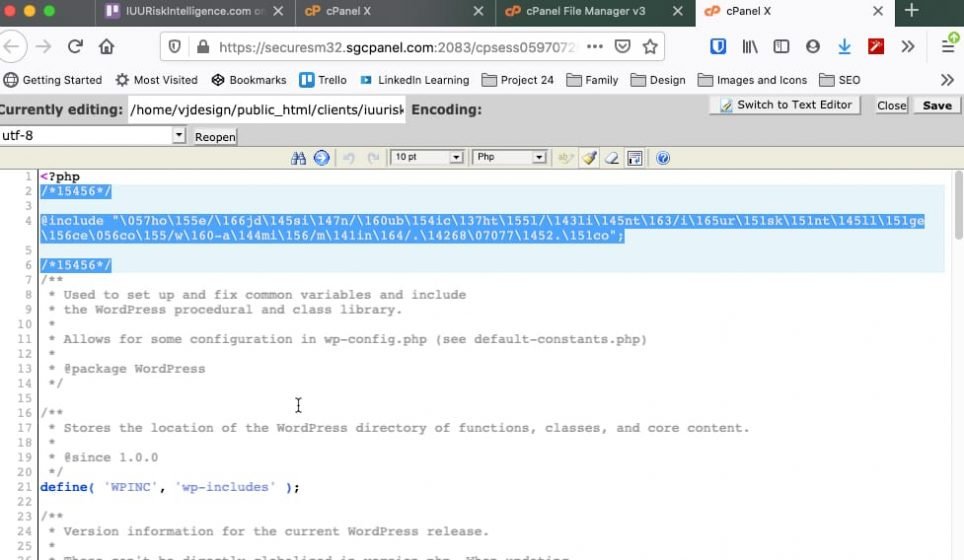
Select the infected code and delete it.
3. Infected file with lots of malicious code
I noticed that some php files were heavily infected. I noticed that such malicious code started on Line 1 before the opening <?php tag on line 1 and before the opening comments. A good indication is that most WordPress (php) file start with detailed comments as indicated below.
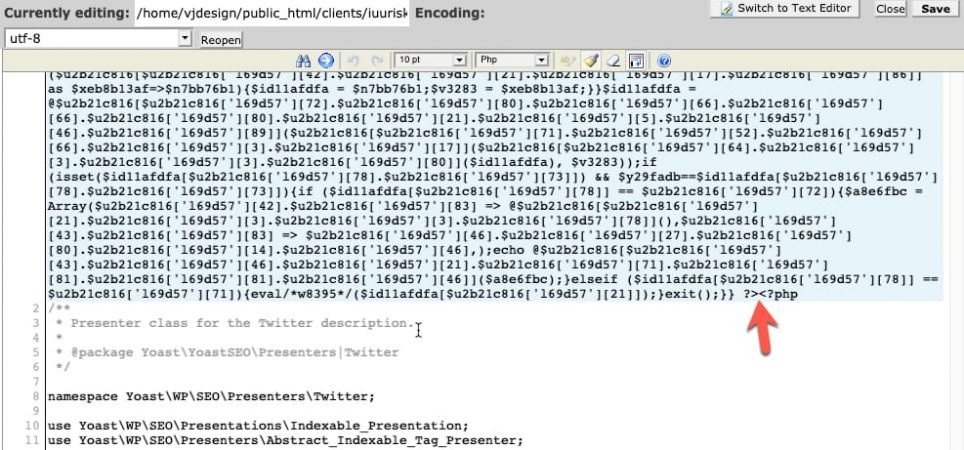
Select the infected code up to the arrow and delete it.
Go through the full list of infected URLs and clean or delete the infected files as required.
Keep your site clean
Having cleaned the infection, contact your web host to make your site ‘active’ again.
However, you will need to ensure that your site is loading and functioning well – at the same time you don’t want hackers to exploit your site if it is not fully clean.
Therefore, you either need to prevent access to your site or password protect the site .
Block all access and allow only your IP address
Open the .htaccess file (using File Manager or FTP) and place the following lines at the top of the file.
order deny,allow
deny from all
allow from IP.IP.IP.IP
Replace IP.IP.IP.IP in the code above with your IP address and save the file.
Password protect the website
To add password protection on your website in SiteGround, go to your Site Tools > Security > Protected URLs. This will make the website only accessible to people who know the credentials for accessing it. For more information, refer to SiteGround Tutorial on How to Password Protect Directories.
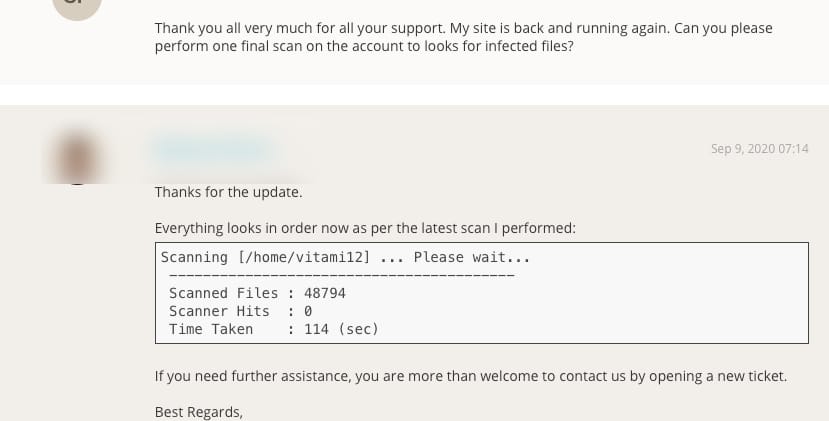
After another check, SiteGround confirmed that there was no more infection.
I installed security plugins to monitor the WordPress installation and database.
I also updated all the plugins, removed the file manager plugin and installed backup plugins to be able to restore the site if it gets hacked in future.
I asked SiteGround staff for another scan a week later which also confirmed that malware was completely removed.
Hope that helps you! Please feel free to ask any questions via comments below.
Read more
- How to Clean a Hacked WordPress Site – https://sucuri.net/guides/how-to-clean-hacked-wordpress/
- 10 Steps to Remove Malware from Your WordPress Site – https://askwpgirl.com/10-steps-remove-malware-wordpress-site/
- How to Remove Malware from a WordPress Site in 2020 – https://www.hostinger.com/tutorials/remove-malware-from-wordpress-site-wordfence

This is a great guide to follow to remove malware from your WordPress site. I would recommend following these steps if you think your site may be infected.
In general your advices are good, but you can’t find all suspicious files. If they are – they are everywhere in wp-admin, in plugins/ uploads and themes folders. What you gonna do? Manually every day check all suspicious files? There are even files with *.jpg , .txt extension. I saw infected file with readme.txt file (all plugins have this file). Sorry this advice isn’t enough
Hi David, Good point. SiteGround provided a full scan for me for free. I went back to them at least 3 times before all infected files were removed – this included some images that had the infection and text files. I asked them for another scan a week later which also confirmed that malware was completely removed. In total they performed 5 free scans for me. I also installed security plugins to monitor the WordPress installation and database. If the infection persists, I would recommend that you pay for Malware removal services from a third party. Hope that helps! Cheers, VJ
I don’t find any good plugin for that. tested 5 plugins, find 30% of malwares. Cpanel based scanner find only 20% of malwares. No more.